My first post this year is from a slightly different angle. I have been studying of late for the AWS Certified Solutions Architect – Associate certification with a view of gaining a greater understanding of native cloud as well as strengthening conversations around VMware Cloud on AWS and connectivity options into the platform.
The study sent me down a rabbit hole, for me there is no better way of learning than seeing/configuration what I have learnt.
I had the following scenario in AWS, a dedicated VPC for my AWS study in the London (eu-west-2) region. I have a subnet configured in each of the availability zones, each of these are private subnets, along with no Internet Gateway (IGW) attached to the VPC. There was a lonely EC2 instance running in the VPC, I set myself the challenge to connect to this on it’s private IP address. I have not configured Amazon SSM, my only way in would be via RDP, over the private IP.
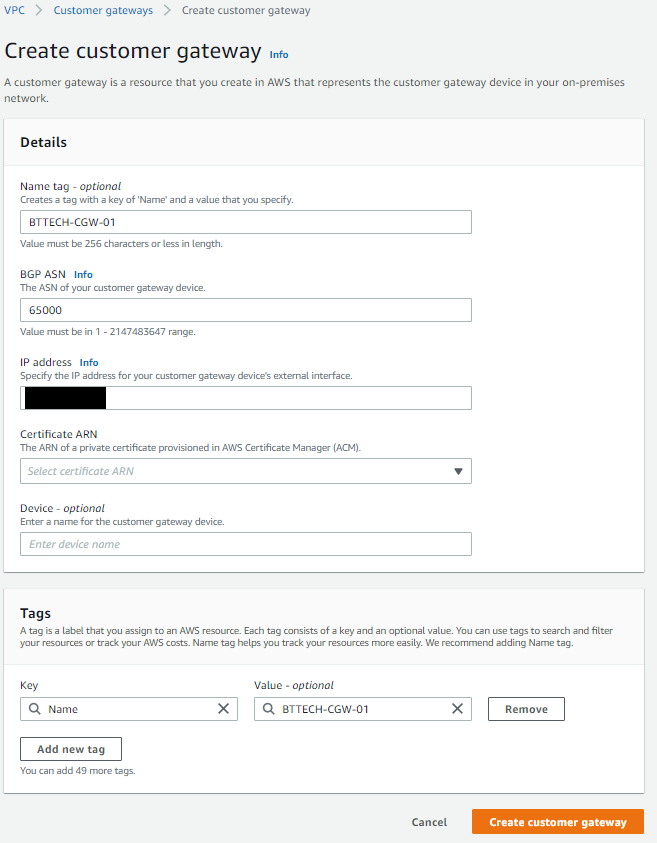
First step was to create my Customer Gateway. This is a representation of where the VPN connection will be initiated from. The Synology RT6600ax doesn’t support BGP so this will be a statically routed VPN for me so I left the ASN as the default of 65000 knowing that I wouldn’t need this. Provided my external IP address, gave the CGW a name for identification and left the reset as default.
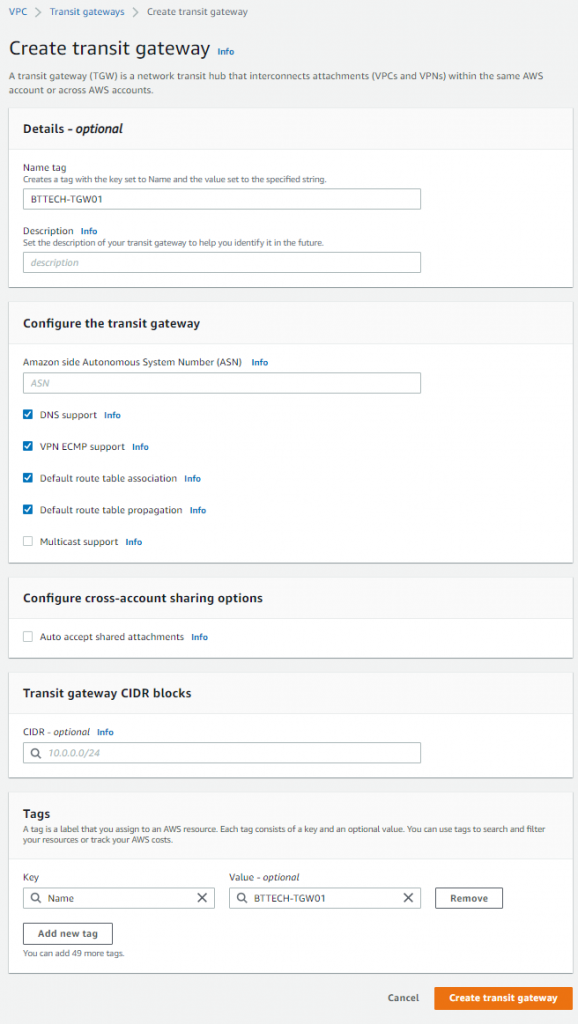
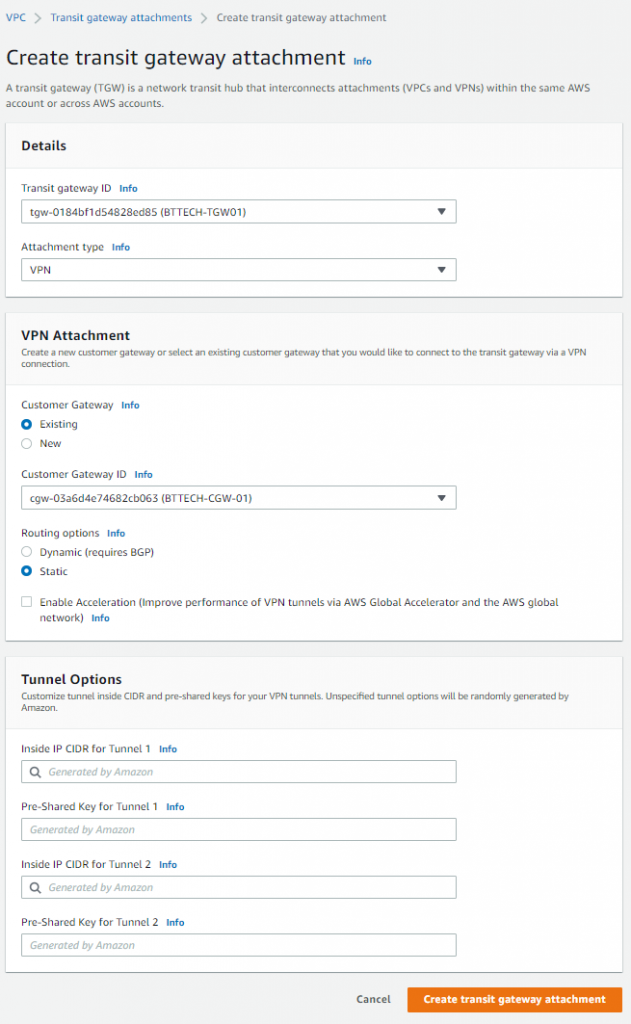
I then created a Transit Gateway that I will use to bridge the gap if you will between the subnets in the VPC, and the VPN connection. Aside from setting a name, I left all other details as default.
I then created a Transit Gateway attachment between the Transit Gateway and Customer Gateway, as per the below. Setting this to static routing, as mentioned the Synology router doesn’t support BGP.
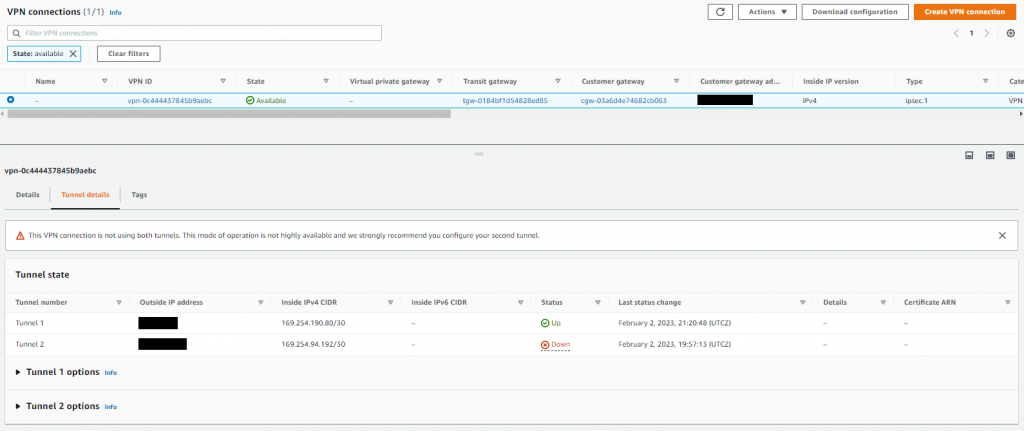
This then in turn creates a Site-to-Site VPN connection, which after a few minutes will show in an available state.
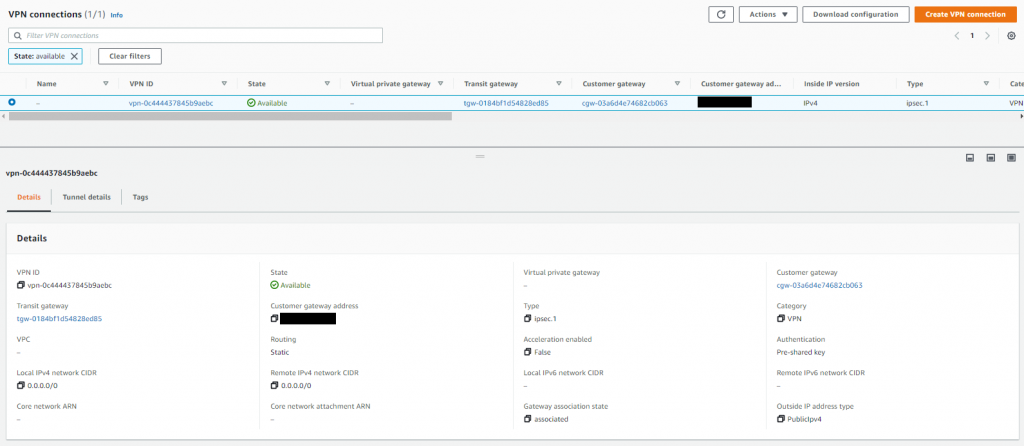
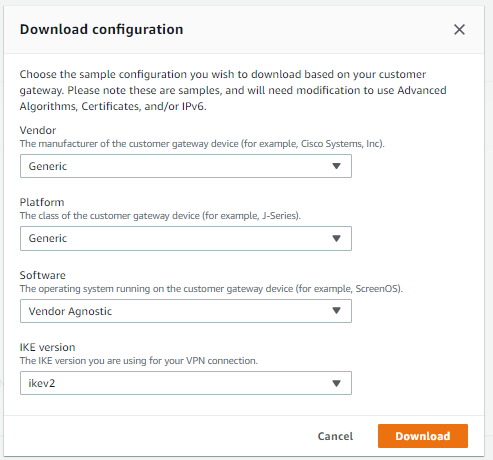
From the Site-to-Site VPN panel, top right, I downloaded the VPN configuration. There isn’t a vendor selection for Synology so I chose generic and set IKE to version 2.
This will provide you with a text file containing all the details you need to establish the VPN connection from your on-prem device.
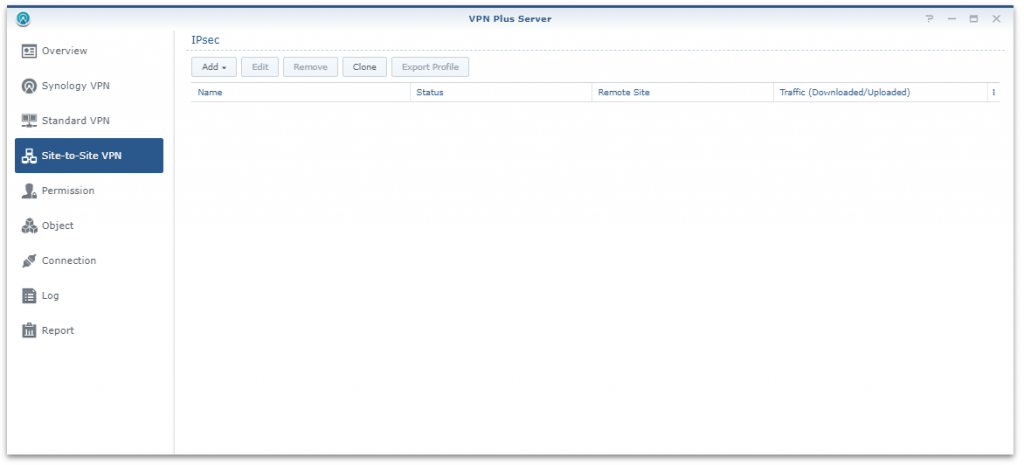
The next step for me was to create the VPN connection from the Synology device. Connected to the router, launch the VPN Plus Server application and navigate to Site-to-Site VPN.
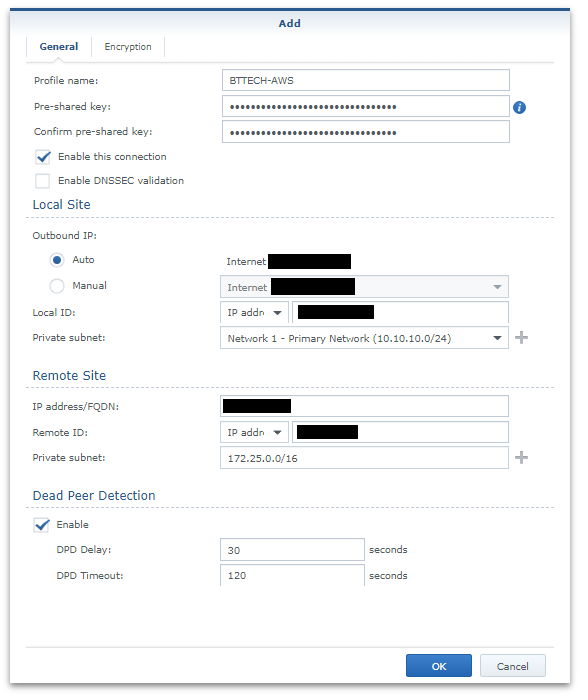
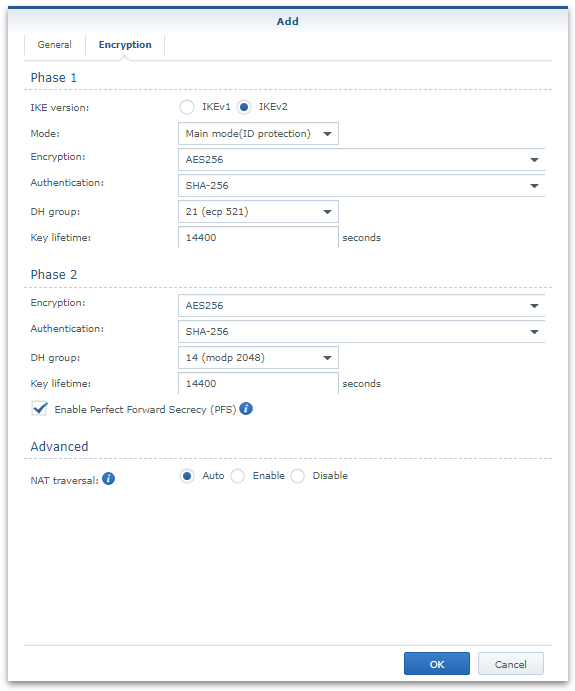
Add a VPN, manually and provide the details on the general tab from the text file downloaded a moment ago from AWS.
Ensure that the encryption settings also match that from the downloaded configuration file as well and then save the configuration via OK,
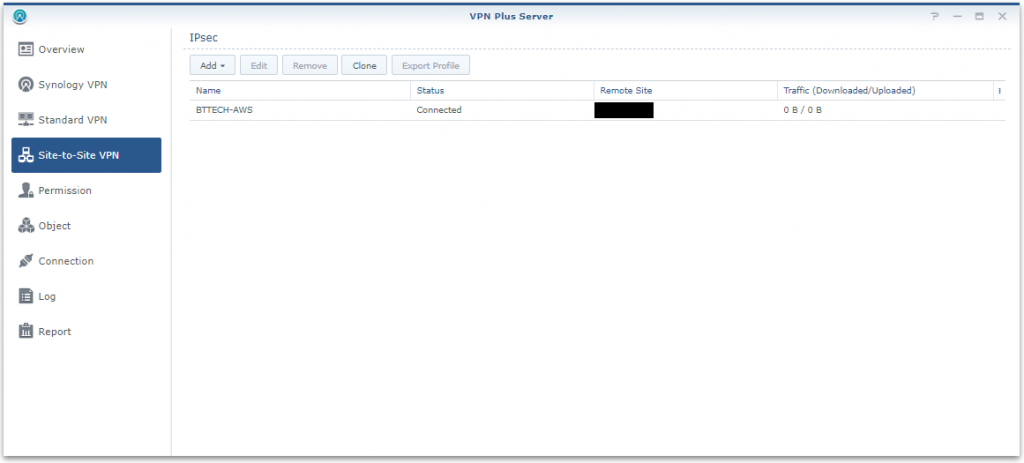
All being well we should then see the VPN in a connected state.
We can also verify this from the AWS side too. Note that for the purpose of my lab configuration I only have a single tunnel configuration. However, you would configure multiple tunnels from different devices on-prem in a production scenario, there is just little point for me having two tunnels from one device.
But, wait, I still cannot get to the internal IP address of my EC2 instance.
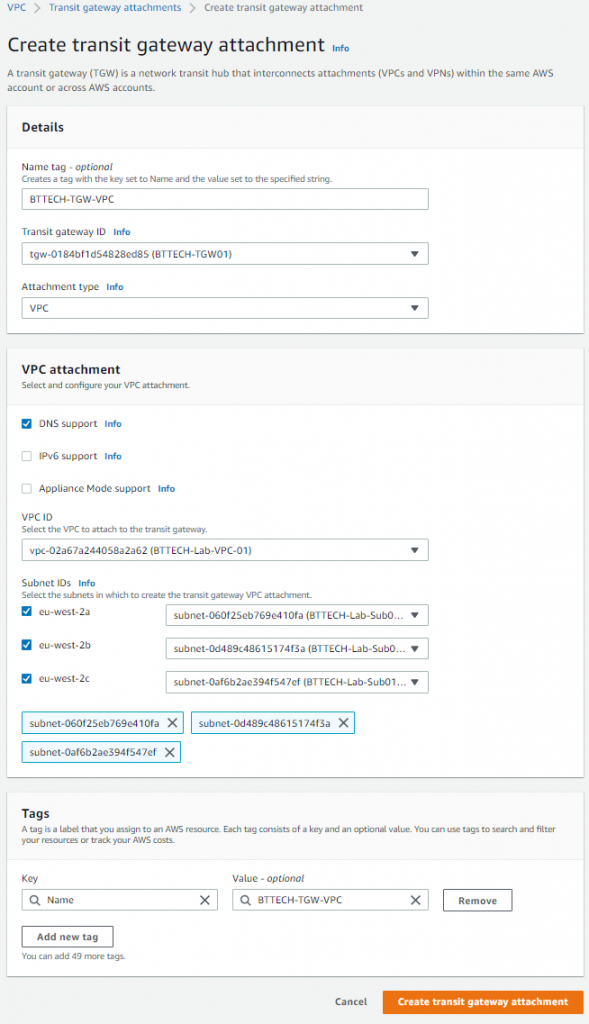
I next need to create another Transit Gateway attachment for the Transit Gateway to the VPC where the EC2 instance resides. I attached this to all 3 subnets in the VPC as well.
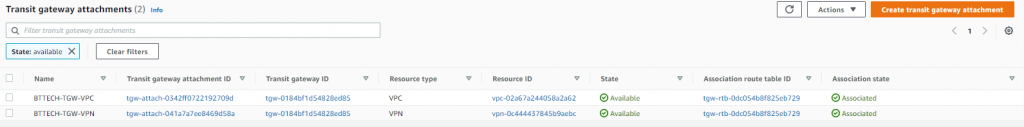
That’s two attachments now, one to the VPC and the other to the VPN.
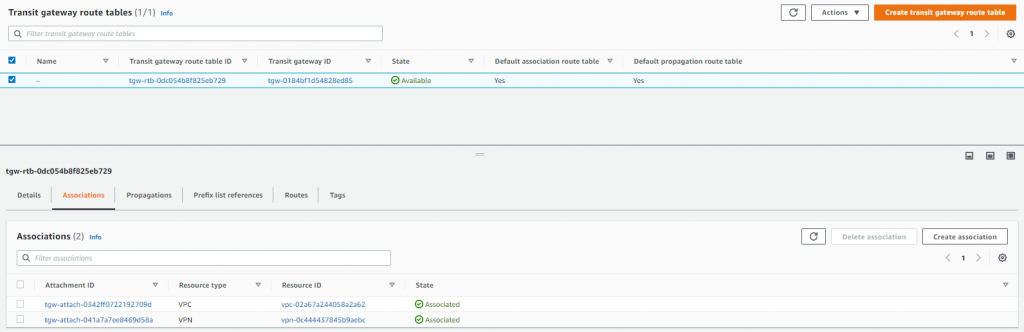
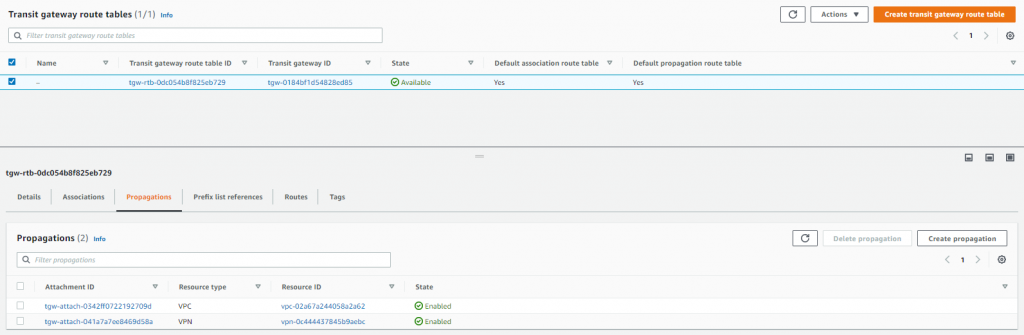
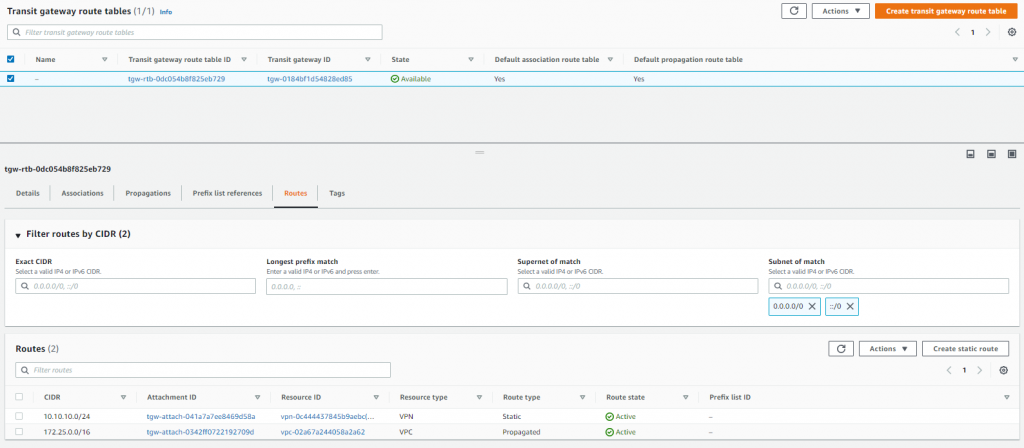
Next step was to check the Transit Gateway route table and just confirm a couple of things, the associations and propagations, these are handled with the attachment but I just wanted check that the VPC and VPN were there.
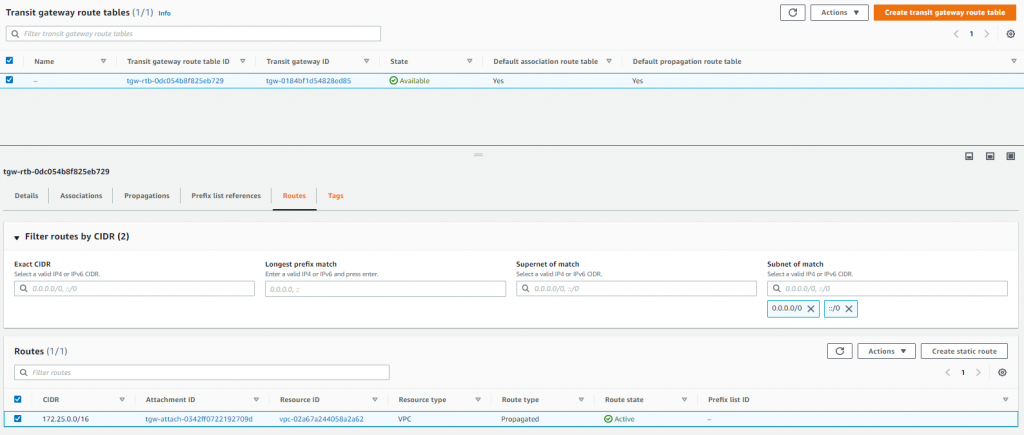
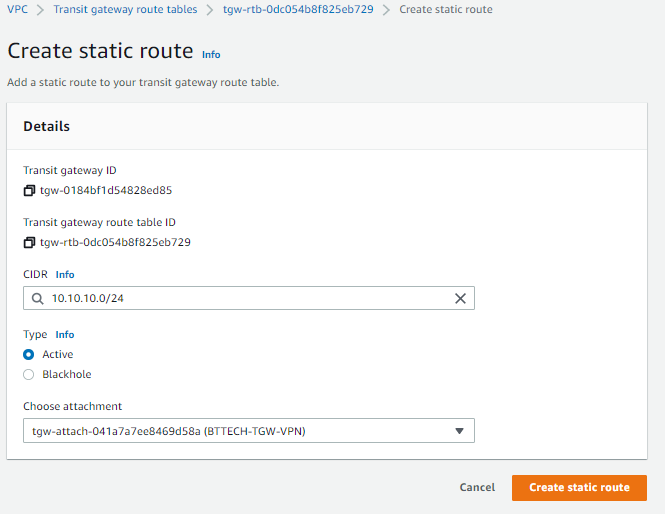
I now had to configure a static route on the Transit Gateway for my local subnet at home.
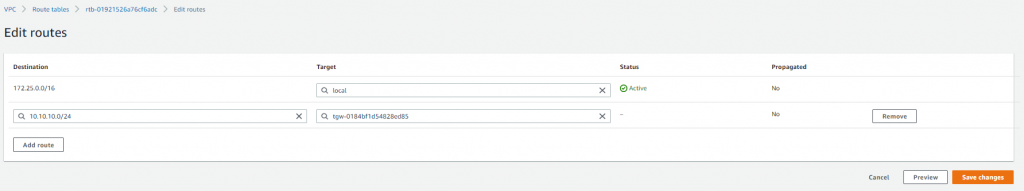
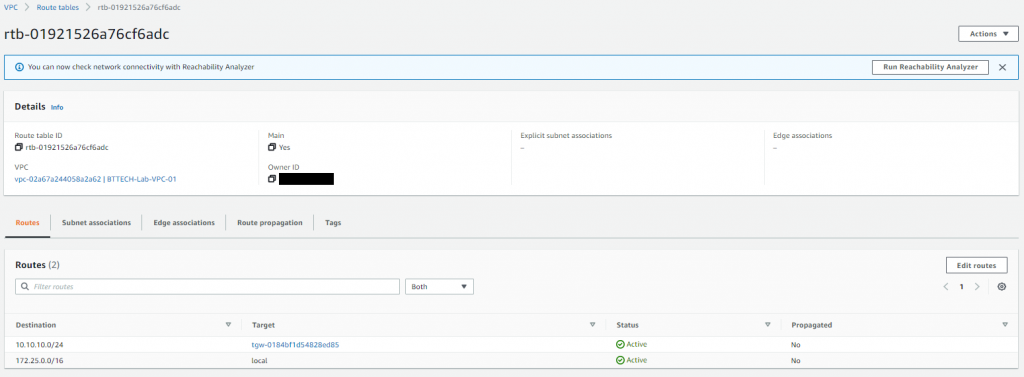
Then just one more step, the route table for the VPC still doesn’t know how to get to my local subnet. A static route was required on the VPC route table to direct the traffic for my local home subnet down the VPN via the Transit Gateway.
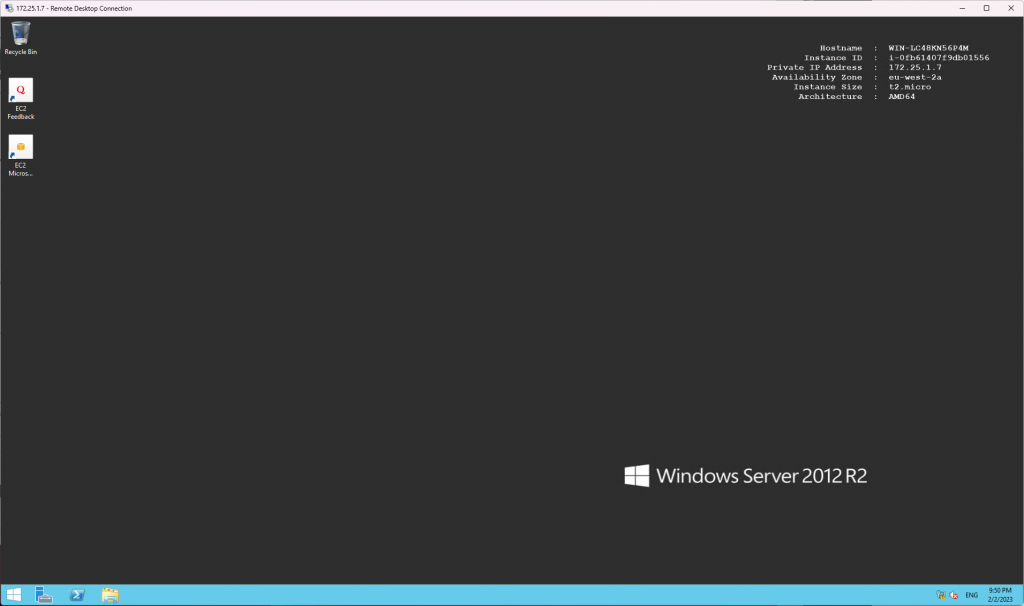
There we have it, routing in place VPN up and I can RDP to the Windows EC2 instance on it’s private IP address.




Laurence
Great article Ben. How come you used a transit gateway rather than a virtual private gateway?
Ben Turner
Thank you Laurence! The virtual private gateway only allows for a connection to a single VPC. With the transit gateway I could attach this to multiple VPC’s, as well as using the same VPN tunnel to connect to a VMware Cloud on AWS SDDC via a transit gateway to a VMware managed transit gateway peering.
Pingback: AWS VPN connection from pfSense using BGP - BTTECH Blog